The internet has launched a new business line for criminals, which has created new headaches for people, police and businesses. They use various fear-based techniques to trick people into doing things, such as sharing personal information (e.g., phishing or spear phishing), which is then sold on black market websites (a.k.a. the dark web).
Internet criminals may also embed software in email attachments that, when opened, will corrupt your files and they’ll demand a ransom (i.e., ransomware) to release it. They can capture keystrokes (e.g., record your passwords, personal details, bank account info) or even enable your computer camera so they can spy on you. I have seen this one in action and it’s easy to do.
I’m not trying to scare you into never using the internet again, but you need to be aware of events on the internet that are happening today. The more you know, the more you can protect yourself against internet security threats.
Many businesses are educating their employees about how to use the internet (including email) safely. At SRC, we have a robust internet security training program. But not all businesses have this and even then, there’s still a large part of the population—grandparents, parents and children—that don’t have access to this type of training.
It’s really on us, those in the know, to talk to our friends and family about how they can stay safe online.
So, what can you do and how can you educate others?
Here are some simple things you can do and share with your friends and family to keep everyone safe.
3 Online Threats to Watch for and What to Do
1. Unexpected email from a “friend”
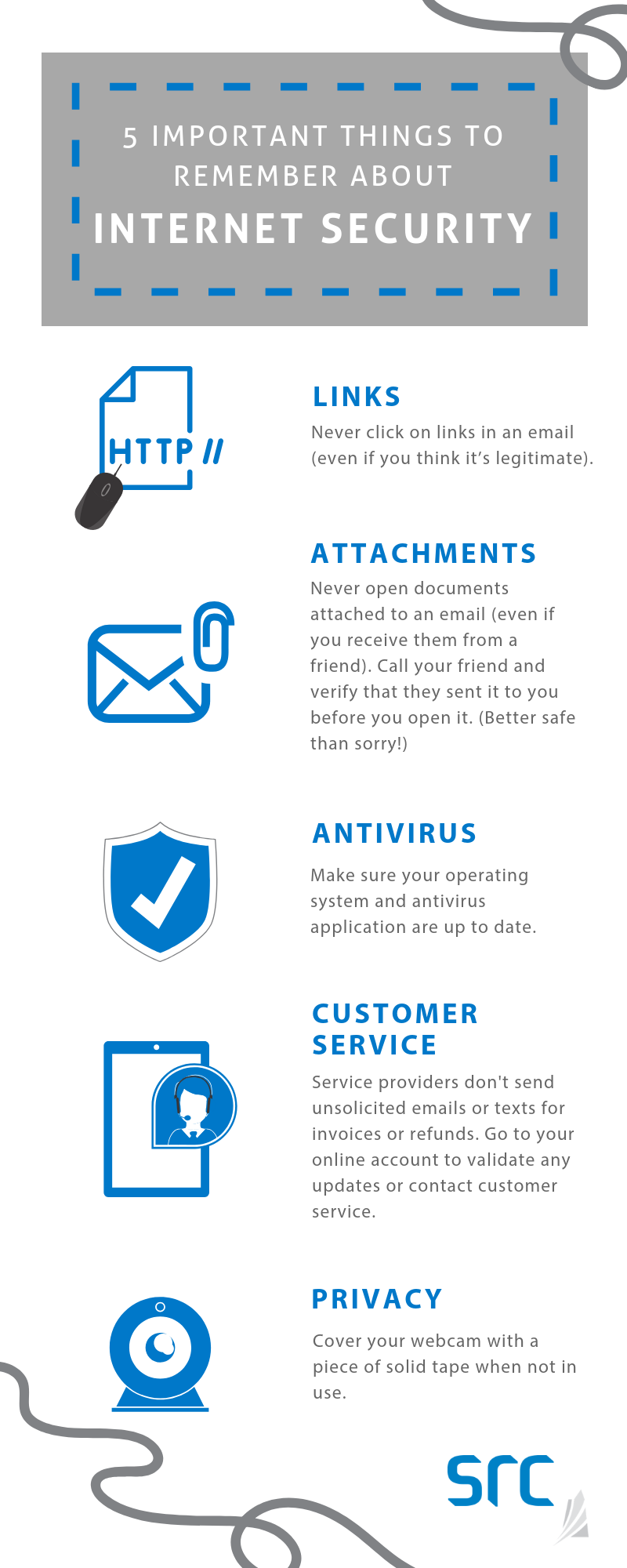
- Event: You receive an unexpected email from someone (usually in the wee hours of the morning) asking you to do something urgently or click on a link.
- Action: Call that person to confirm they sent you the email. You can also hover over any links in the email (on desktop, using your mouse and on your mobile device, by pressing and holding down on the link) to see if the link is for a website that is not related to the message. It’s strongly recommended that you call the sender to confirm.
- Background: Typically, these types of emails from a “known” person indicate their computer/email has been hacked and the hacker is using their email address and contact list to “phish” for information from you.
2. Unexpected email from a “service provider”
- Event: You receive an unexpected email from a service provider (e.g., Apple or Netflix) that you may have done business with in the past, indicating your purchase or refund just went through. They usually include an attachment (e.g., an invoice).
- Action: Don’t click on any links or attachments. Most service providers have a website where you can check your account. Open your browser and type in the address for that website, login and review your transactions (most likely there are no new transactions). If you’re not sure, contact customer service using the information provided on the service provider’s website.
- Background: Hackers typically use big name service providers, such as Amazon and eBay, to trick you into thinking their email is from a trusted company.
3. Unexpected text message on your phone
- Event: You receive a text message from a service provider saying you are getting a refund and to click on the link in the text message.
- Action: Delete the message. Service providers do not provide refunds this way.
- Background: Texting is the latest way to anonymously contact you and try to entice you to click on a link and provide information (this one is called smishing). You can block phone numbers if you keep getting hassled. Check with your device manufacturer.
Regular computer Maintenance (Yes, just like your car!)
1. Make sure you have configured your computer to automatically install operating system (e.g., Microsoft or Apple) updates as they continue to fix problems that the bad guys can exploit. Contrary to popular belief, all operating systems are at risk.
2. Always have an antivirus application installed on your computer and make sure that it is set to automatically update.
- On some of the more advanced antivirus applications, you can (and should) also turn on “intrusion detection/protection,” “process protection” and “boot time protection.”
3. Change how your computer looks up internet addresses (this is called a domain name system or DNS – kind of like a phonebook for computers):
- Change your DNS on your home router and mobile device to use the free Cisco OpenDNS (Umbrella) DNS servers. Here’s how to set it up.
- By setting this up, the links you might click on are checked against Cisco’s list of bad addresses and Cisco may prevent you from going to unsafe websites.
- Cisco uses artificial intelligence to monitor trends on the internet and identify bad servers as they are built. Once they have found one, they automatically block it so that you don’t accidentally go to a bad site. The system isn’t perfect, but it’s another level of protection and it’s free.
4. Backups (I can’t stress enough about the importance of backing up your home computer – remember all your family photos are probably stored there now.)
- If you use an Apple computer, it comes with an application called Time Machine that will take snapshots of your data and restore it should you lose a file or your hard drive crashes.
- Cloud applications: There are some great cloud storage companies that provide real-time backup services for storage in the cloud (servers on the internet somewhere) at varying price levels. For a small fee, you can get quite a bit of storage space. More expensive providers will give you additional options for restoring and accessing your data. Here is PCMag’s Aug 2018 rating of some of them.
- External hard drive: You can purchase an inexpensive external hard drive (that plugs into your computer) with a lot of storage space. Only plug it in for backups and then unplug it from your computer to keep your data safe. (Note: You should enable your computer to back up at a certain time automatically, so you don’t have to remember to do it.)
This post was co-written by former SRC employee, Chuck Ingerman.